North Korea targets crypto firms

North Korean hackers are using sophisticated Mac malware delivered through fake Zoom invites to break into Web3 and crypto firms, stealing sensitive data while evading standard security measures.
Security researchers have identified a sophisticated campaign by North Korean-aligned hackers using novel malware to target Web3 and cryptocurrency companies on macOS systems.
The SentinelOne Labs report describes a multi-stage attack chain. This attack chain combines social engineering, deceptive AppleScripts, and binaries compiled in the Nim programming language.
Nim is uncommon on macOS, which complicates detection. The operation, dubbed “NimDoor,” demonstrates evolving tactics by DPRK threat groups to compromise security defenses and steal sensitive data from crypto-focused businesses.
How the attack works
The initial compromise often begins with social engineering. Attackers impersonate trusted contacts over Telegram and lure victims into scheduling Zoom calls via Calendly links.
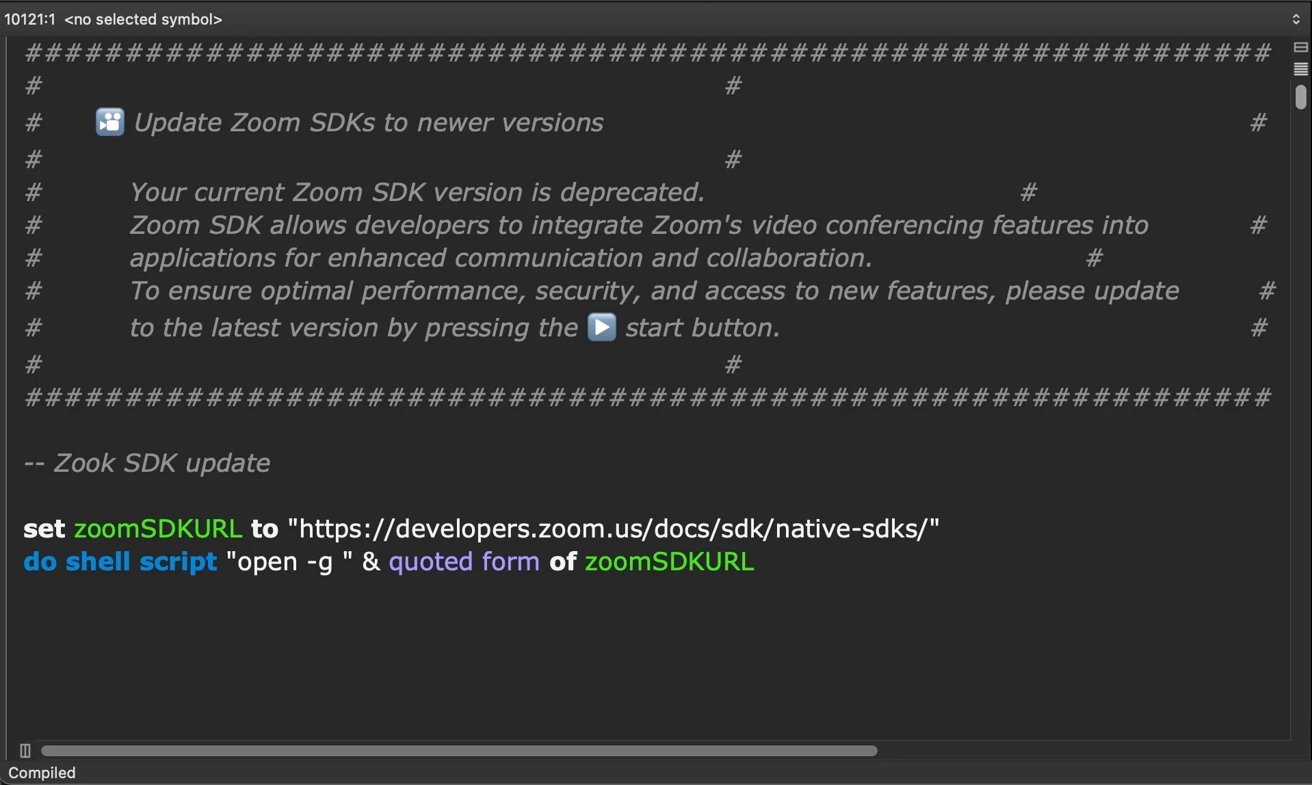
The zoom_sdk_support.scpt file contains 10,000 lines of padding with a typo reading “Zook” instead of “Zoom.” Image credit: SentinelOne
Victims receive phishing emails with malicious Zoom SDK update scripts that are booby-trapped AppleScript files. These scripts have thousands of padding lines to evade detection and fetch additional malware from attacker-controlled servers that mimic legitimate Zoom domains.
Once executed, these scripts download further payloads to the victim’s machine. Researchers found two primary Mach-O binaries — one written in C++ and another in Nim — deployed in tandem to maintain persistent access and steal data.
The malware uses unusual techniques for macOS, such as process injection with special entitlements. It also employs encrypted communications over TLS-encrypted WebSockets (wss) and signal-based persistence mechanisms.
These mechanisms reinstall the malware when a user tries to terminate it or when the system reboots.
Advanced data theft and persistence
Data exfiltration is accomplished through Bash scripts that scrape browser history, Keychain credentials, and Telegram data. Targeted browsers include Arc, Brave, Firefox, Chrome, and Microsoft Edge.
The malware also steals encrypted local Telegram databases for potential offline cracking.
Persistence is achieved through clever use of macOS LaunchAgents and deceptive naming conventions. For instance, the malware installs binaries with names like “GoogIe LLC,” substituting a capital “i” for a lowercase “L” to blend in with legitimate Google files.
Another binary, “CoreKitAgent,” monitors system signals to reinstall itself if terminated. It includes anti-analysis measures such as 10-minute asynchronous sleep cycles to thwart security sandboxes.
Binary Ninja’s MLIL view shows how the malware processes commands. Image credit: SentinelOne
According to SentinelOne, the use of Nim for these binaries represents an evolution in threat actor tooling. Nim’s compile-time execution and interleaving of developer and runtime code make static analysis more difficult.
AppleScript-based beaconing provides lightweight command-and-control. It does so without relying on heavy post-exploitation frameworks that could more easily trigger alerts.
How to stay safe from NimDoor
Users should avoid running scripts or software updates received through unexpected emails or messages, even if these appear to come from trusted contacts. Careful inspection of URLs is important because attackers often craft lookalike domains to trick victims.
Next, keep macOS and all installed applications updated with the latest security patches. Updated apps reduce vulnerabilities that malware campaigns exploit.
It also helps to use reputable endpoint security tools that can detect suspicious behaviors like process injection, malicious AppleScripts, or unrecognized launch agents. Reviewing login items and LaunchAgents on a regular basis can reveal unauthorized entries that maintain persistence.
Finally, adopt strong, unique passwords and enable multi-factor authentication where available.

