A rare iPhone crash linked to an iMessage image handling and sharing bug may have been the first sign of a targeted spyware attack, according to new forensic evidence — but Apple is skeptical.
A newly revealed iMessage bug in iOS, now patched, may have exposed some iPhone users to silent surveillance attempts. The flaw, discovered by the security firm iVerify, affected how iPhones processed nickname updates in the Messages app.
The security researchers say they found signs of possible exploitation on the devices of journalists, government officials, and tech executives. Apple, however, strongly denies that the bug was used maliciously.
The vulnerability, which researchers named “Nickname,” was quietly fixed in iOS 18.3.
What the Nickname vulnerability did
The issue was tied to the Share Name and Photo feature. This setting allows users to send their preferred name, profile picture, and wallpaper when messaging others.
According to iVerify, a flaw in how iOS handled these nickname updates made it possible to crash the Messages app remotely. Attackers could send a specially timed series of nickname changes, triggering a memory error in a system process called “imagent.”
This type of flaw could potentially be used as a starting point for a more serious attack. No interaction was required from the user.
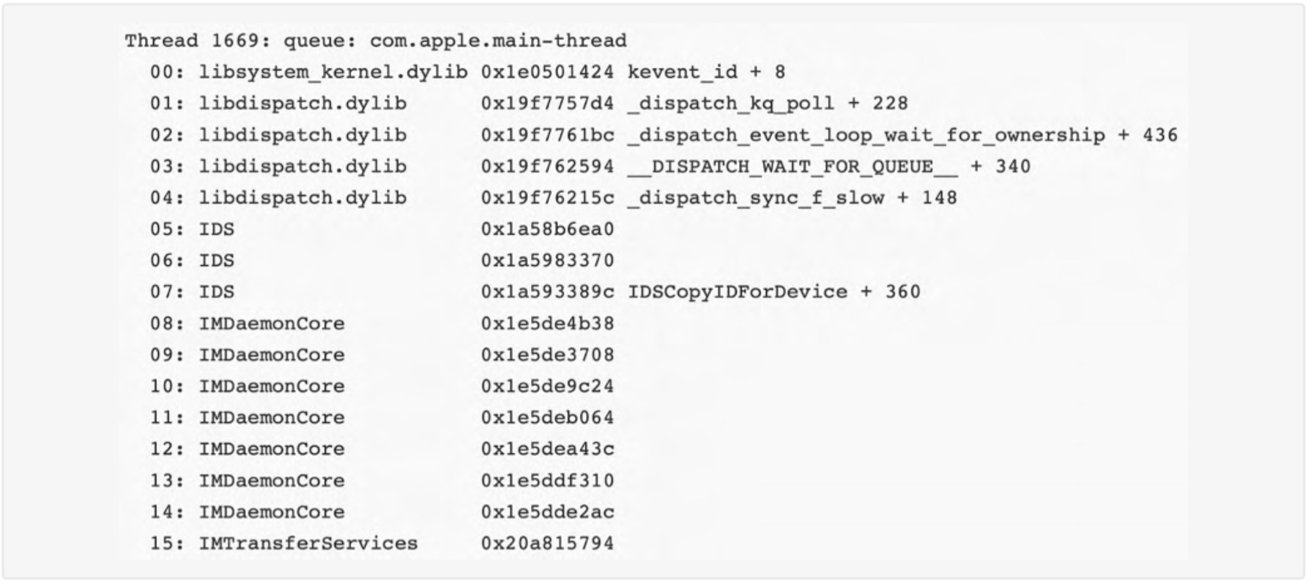
Partially decoded crash from iOS 17.6.1, similar to other imagent issues. Image credit: iVerify
That’s why this kind of vulnerability is referred to as zero click. The only things a potential attacker needed was the target’s phone number and Apple ID.
Evidence of possible targeting
Between April 2024 and January 2025, iVerify analyzed crash logs from nearly 50,000 iOS devices. The type of crash associated with the Nickname bug was extremely rare.
It appeared on fewer than 0.002 percent of the devices studied, and only on phones used by people with elevated risk profiles.
One senior European Union official experienced a crash consistent with the vulnerability and received a threat notification from Apple about a month later. Another device showed signs of file deletion just 20 seconds after a crash.
Researchers from iVerify say this pattern resembles what has been observed in past spyware attacks. The team didn’t find any malware or implants. They say they have moderate confidence that the bug may have been used as part of a larger exploit chain.
Apple responds with skepticism
Apple disagrees with iVerify’s conclusions. In a statement to AxiosIvan Krstic, head of Apple Security Engineering, said the company strongly disagrees with the claim that this was a targeted attack. Apple believes the crash came from a conventional software bug that was fixed in iOS 18.3.
Krstic added that Apple has seen no credible evidence the bug was exploited in real world attacks. He also said iVerify did not provide technical proof that spyware was installed.
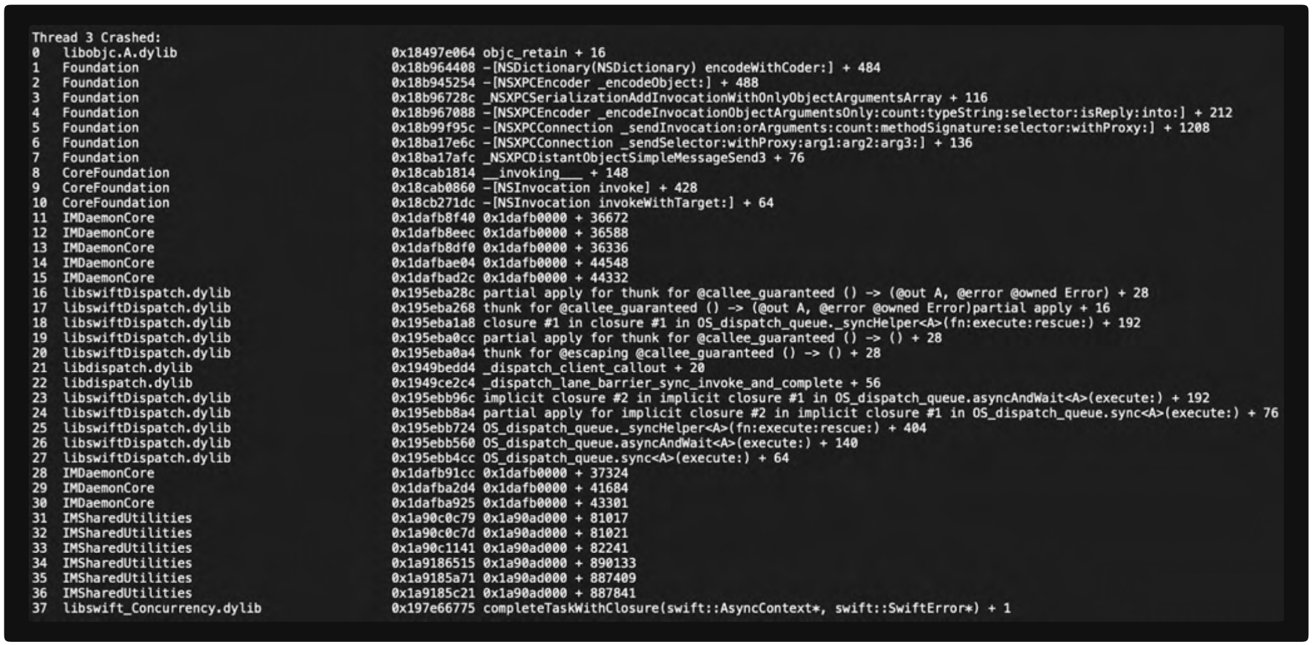
Unprocessed crash data from the Messages system on iOS 17.7. Image credit: iVerify
That’s a significant difference in interpretation. The iVerify company relies on crash logs and patterns of device activity. Apple argues that those findings are not enough to support the idea of an actual attack.
Even without confirmed malware, the Nickname report shows how powerful messaging features can create new risks. It also highlights the challenge of protecting users from invisible attacks that require no interaction.
Apple iMessage already uses advanced security features like BlastDoor to screen incoming data. But this report shows that determined attackers continue to find ways around those defenses.
For users, the takeaway is simple. Keep your device updated, be cautious about unknown messages, and consider extra protections if you work in a sensitive field.
How to stay safe
To reduce your risk from vulnerabilities like Nickname, the most important step is to keep your iPhone updated. Always install iOS updates as soon as they become available.
You can also turn on automatic updates in Settings under General and Software Update to make sure you stay protected without having to remember.
If you work in a high-risk field such as journalism, government, activism, or cybersecurity, consider enabling Lockdown Mode. The setting restricts certain message and web features to help guard against targeted attacks.
It’s also wise to avoid interacting with suspicious messages, even if they seem harmless or come from unknown senders.
For additional awareness, check Apple’s official security updates page. You don’t need to panic, but staying current with software updates is the best way to protect your iPhone from silent threats like this one.

